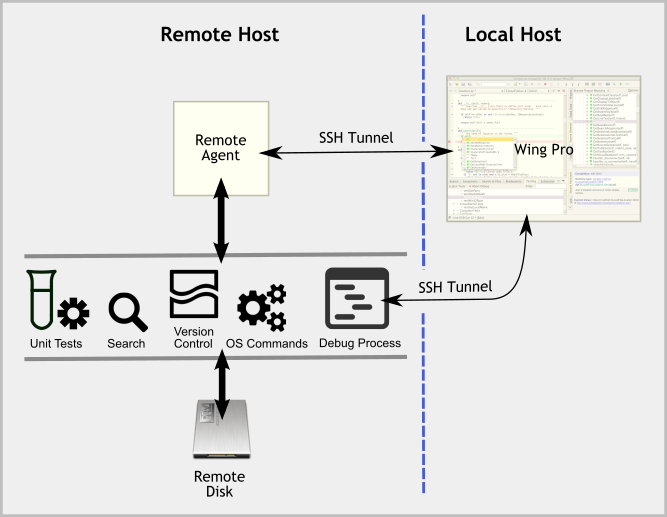
Ssh-agent creates a socket and then checks the connections from ssh. Everyone who is able to connect to this socket also has access to the ssh-agent. The permissions are set as in a usual Linux or Unix system. When the agent starts, it creates a new directory in /tmp with restrictive permissions. Inserting directly into ssh-agent insulates users from sensitive credentials. If a user wants to connect from a different device it’s easier for them to run step ssh login there than it is to exfiltrate keys from ssh-agent and reuse them. There are lots of possible variations of this flow. Just use ssh-agent on your machine to. Enter the passphrase for your ssh private key once. All subsequent calls that need your ssh key will use the saved.
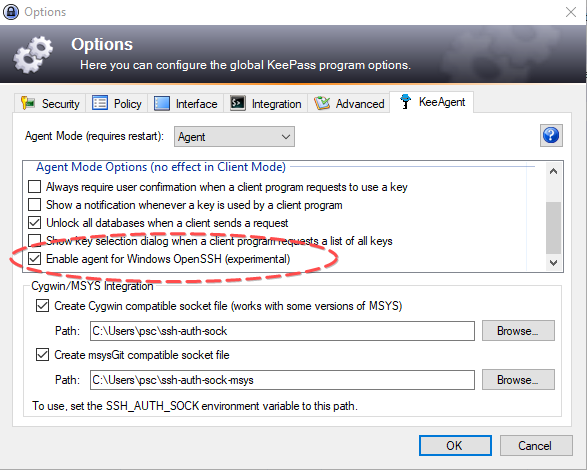

Ssh Use Agent Forwarding

sudo gconftool-2 --direct --config-source xml:readwrite:/etc/gconf/gconf.xml.mandatory --type bool --set /apps/gnome-keyring/daemon-components/secrets FALSE
sudo gconftool-2 --direct --config-source xml:readwrite:/etc/gconf/gconf.xml.mandatory --type bool --set /apps/gnome-keyring/daemon-components/pkcs11 FALSE
sudo gconftool-2 --direct --config-source xml:readwrite:/etc/gconf/gconf.xml.mandatory --type bool --set /apps/gnome-keyring/daemon-components/ssh FALSE
echo $SSH_AUTH_SOCK #copy the path that is displayed as a result

Ssh Use Agent Download
#whenever you want a new shell:SSH_AUTH_SOCK= ssh xxx@2.2.2.2
